How not to secure your server room #1
Here we have a Siemens codelock K42 which is also sold as a Vanderbilt V42 and Bewator K42. Apparently it’s the best-selling codelock in the world. They are very popular in the UK and can be found securing server rooms, banks, strong rooms, schools, hospitals, council buildings, police stations and many more.
If you have a K42 / V42 don’t even bother wasting time reading this just get it removed ASAP. The lock looks the part but is absolute garbage and offers no security what so ever, continue reading to find out why (I will save the best for last).

I bought my K42 for £15 on ebay, no key was supplied and the lock was seized up. Which leads me on to the first vulnerability which is the key way. The key way is far too easily accessible on the front of the unit and uses a tubular cabinet lock of low quality. The lock can easily snapped off using a screw driver as I did. Tubular locks offer no protection as they can be picked with a £20 tubular lock pick just as quickly as using a key and with just as little skill.

The manufacturer claims the tubular lock is high security, which it is not in anyway what so ever. The lock uses standard pins and only has 4 pins instead of the standard 7. If you take a look at the bottom case of the codelock you will likely find a sticker, and on there you will see a section that says key number. Once you have the key number do an Ebay search for K42 along with the key number and you will be able to order the key with no questions asked. There are only 52 possible keys.
Once you have openend the lock by what ever method you choose you will see inside there is a section on the circuit board labelled code-1 and code-2. The yellow jumpers are what set the code for the keypad. You can have two separate 4 digit codes. So if you can open it you know the codes. Alternatively you can just short out terminal 3 and for 4 or 3 and 5 depending on how it is wired up and the door will open. There are no tamper switches in this model, even if there where you can guarantee they are not connected.
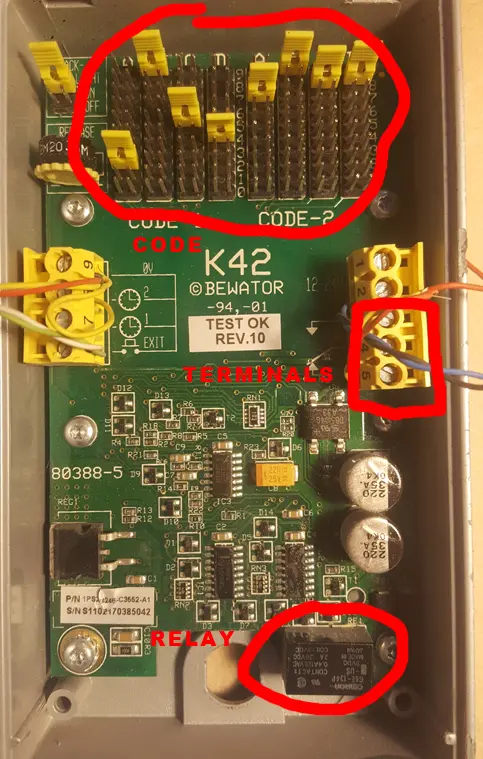
If you take a careful look at the lower right of the image you will see a relay which is basically an electromagnet. What would happen if we supplied our own magnet for the relay, well let’s find out?
I have connected an LED in place of a door release mechanism so you can see when the door would be open.

Lets have some fun with magnets. If you place a largish N52 neodymium magnet at the lower left of the K42 / V42 the relay will switch and the door will open.
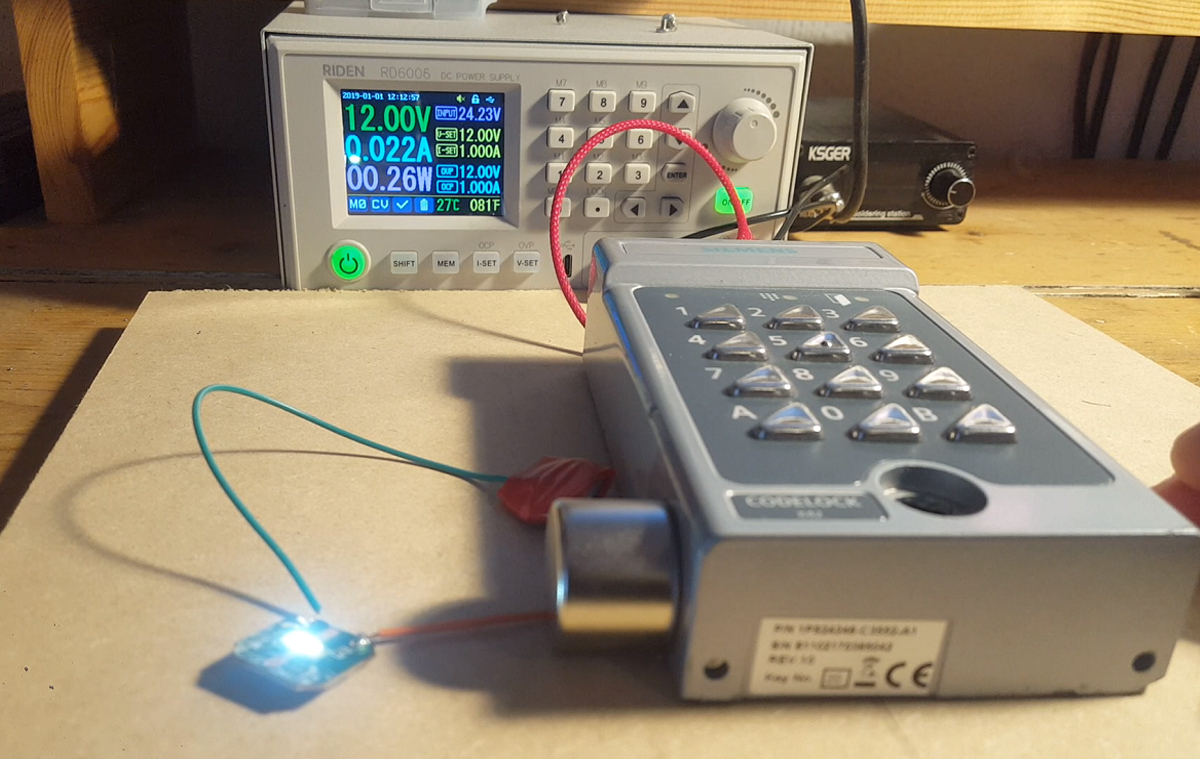
Well I am not done with this piece of crap lock yet. With this lock there are two 4 digit codes giving a total of 10,000 possible codes for each code. This gives a total of 40,000 key presses, and as there are 2 codes this greatly increases are chances of getting a correct code.
The lock uses a basic shift register so using a de Bruijn sequence we can get the total number of keypresses down to 10,000 or the equivalent of 2,500 codes, but as there are 2 possible codes our chances of getting a correct code are greatly increased.
The shift register allows you to type in for example 12345678 and gives you valid codes of 1234, 2345, 3456, 4567, and 5678. A de Bruijn sequence allows you to permutate every code in one sequence without repeating any codes.
Brute forcing the code would require a great deal of technical skill, but with some off the shelf hardware and possibly using mini solenoids it would be feasible. Brute forcing would take a maximum 30 minutes.
If you want to find out more about the de Bruijn sequence then follow the link https://en.wikipedia.org/wiki/De_Bruijn_sequence